I use Office365 for email and other bits and pieces, and I have Azure AD included. While digging around the Proxmox interface, I found the option of authenticating Proxmox with Azure AD. So, how do you do it?
First, go to portal.azure.com and login. To the Azure AD section and, assuming you have an Azure AD setup, select App Registration in the side bar and select New Registration.
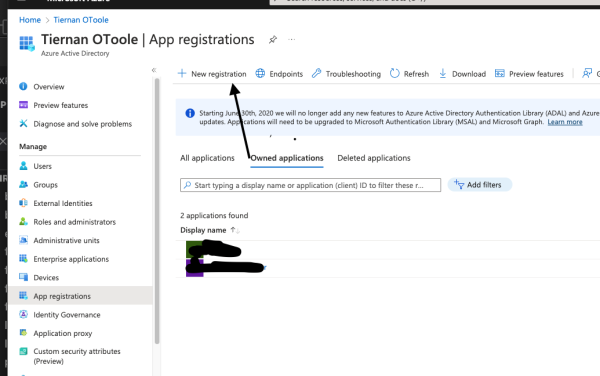
Next Enter a name for your proxmox application, make sure Accounts in this org directory is selected and enter the url of your proxmox server. Make sure application type is set to Web:
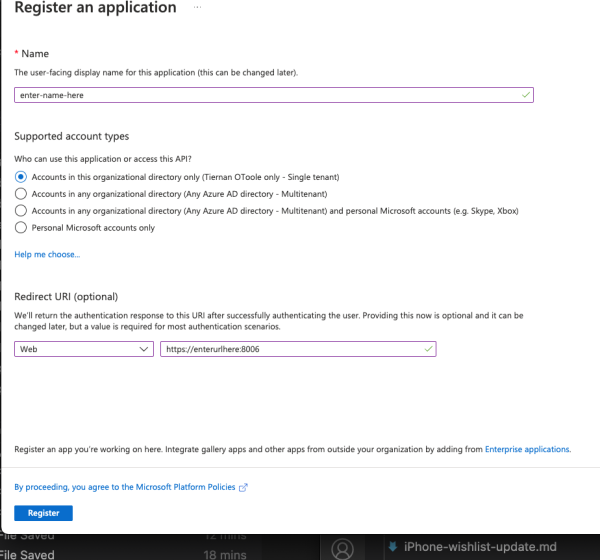
Click Register, and on the next page, select Certificates & secrets. Click new client secret:
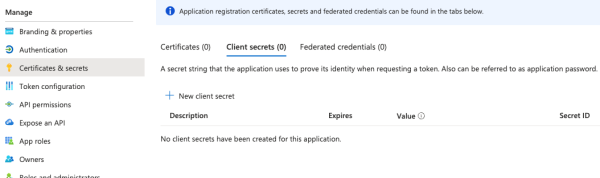
Enter a name and a expiry date.
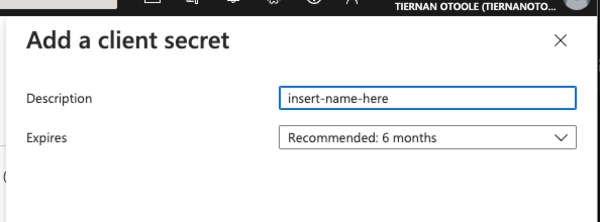
you will need to take note of the value of the secret.
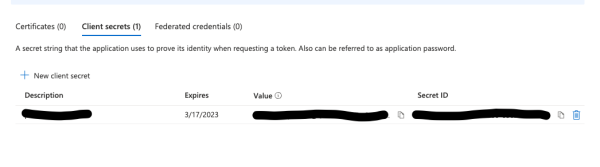
Back under overview, take note of the Application (client) ID and then click Endpoints.
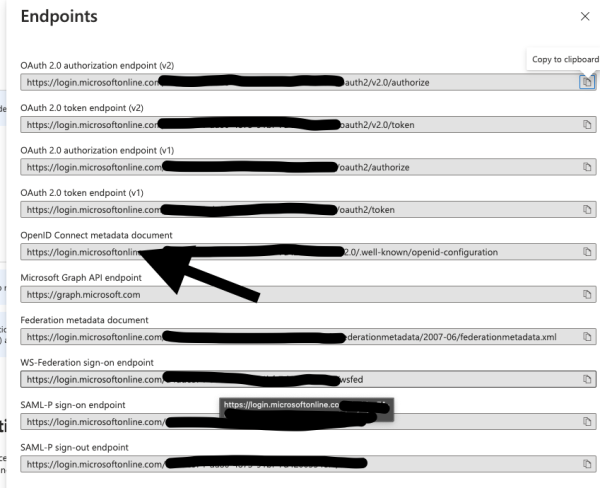
take the URL from the OpenID Connect section, removing the /.well-known/openid-configuration part. The url should look like:
https://login.microsoftonline.com/<yourid>/v2.0
Next, login to your Proxmox server, and under data center, select Realms. Select add and Open ID Connect.
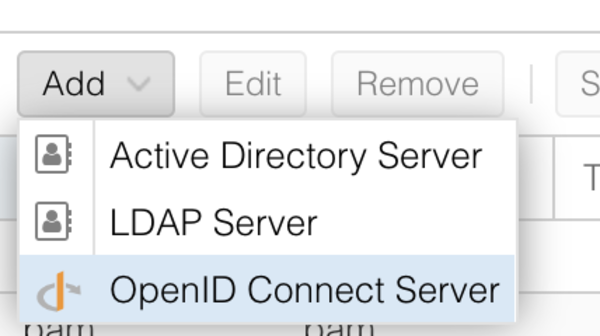
Issuer URL is the URL from the Endpoints. Set the Realm name as you want, enter the Client ID and Key and tick the box for Auto Create Users and Default. Then hit add.
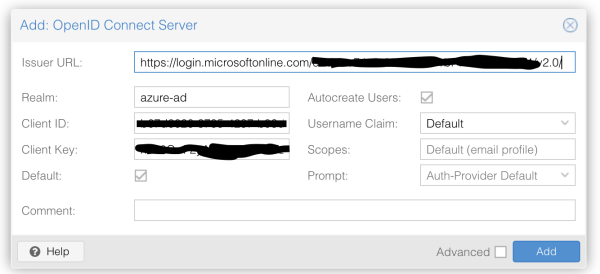
Log out, and login with the new Realm. It will redirect you to the Azure Ad login, ask do you approve (if already logged in) and then redirects you back. At this stage, you cant see anything…
Log back out and in as your default admin user, click the Permissions section and click add:
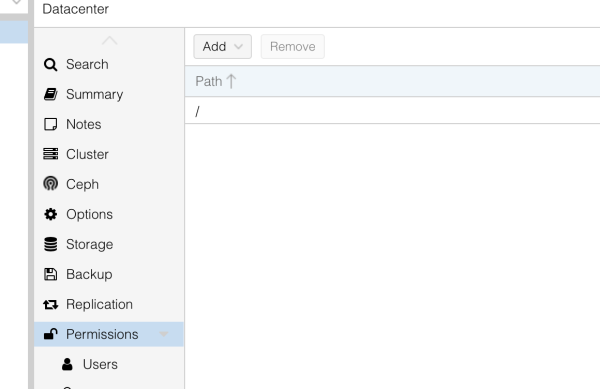
Select User Permissions
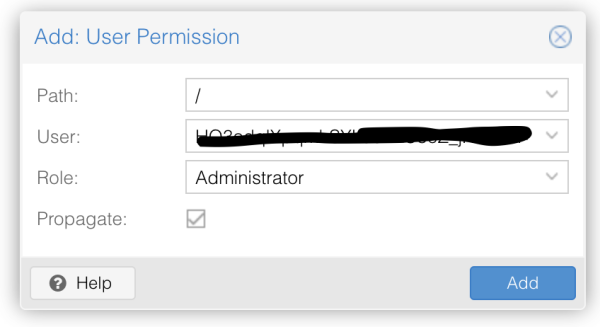
find you user and give them the required access.
Log out, select Azure AD and log back in as your user, and heay presto, you are now in will full admin access! Happy Days!